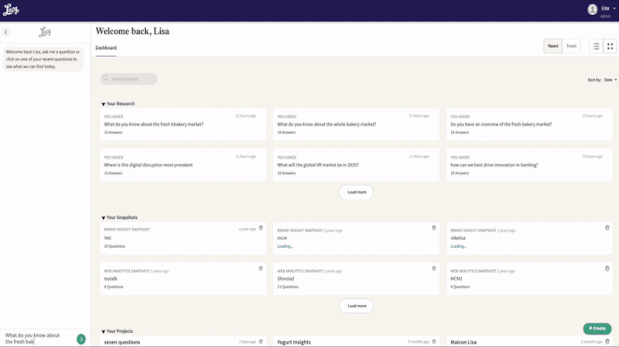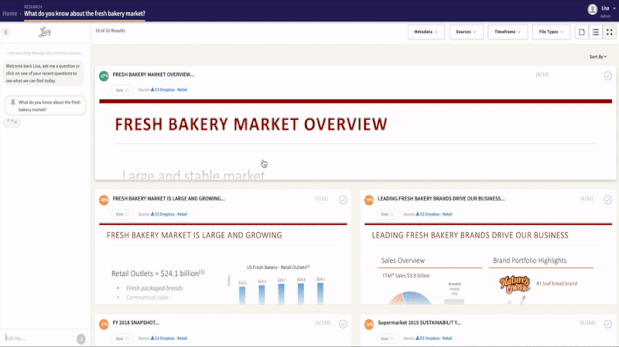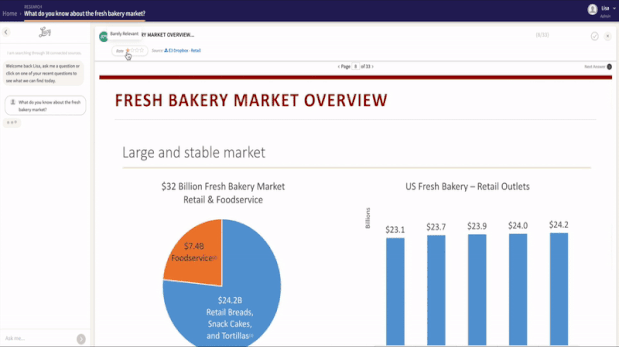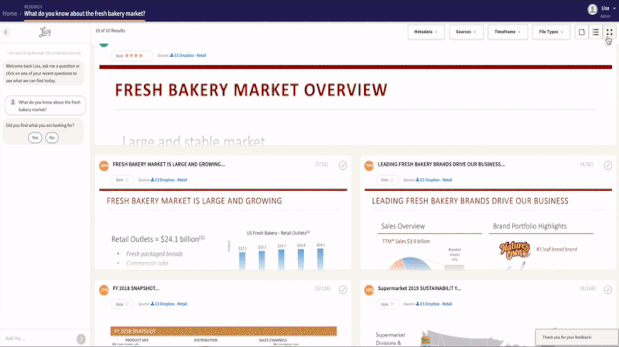
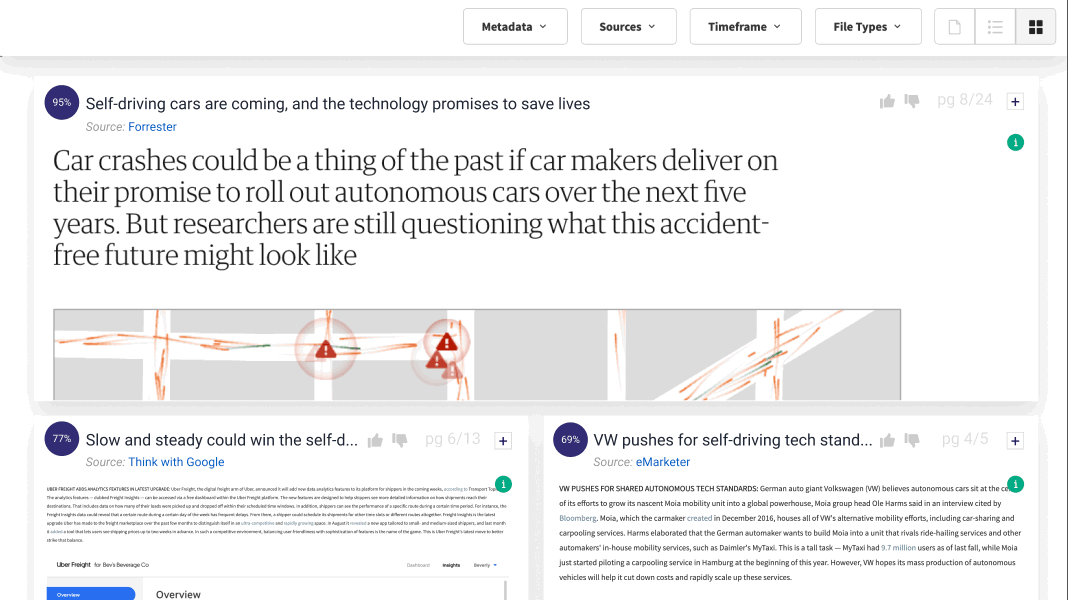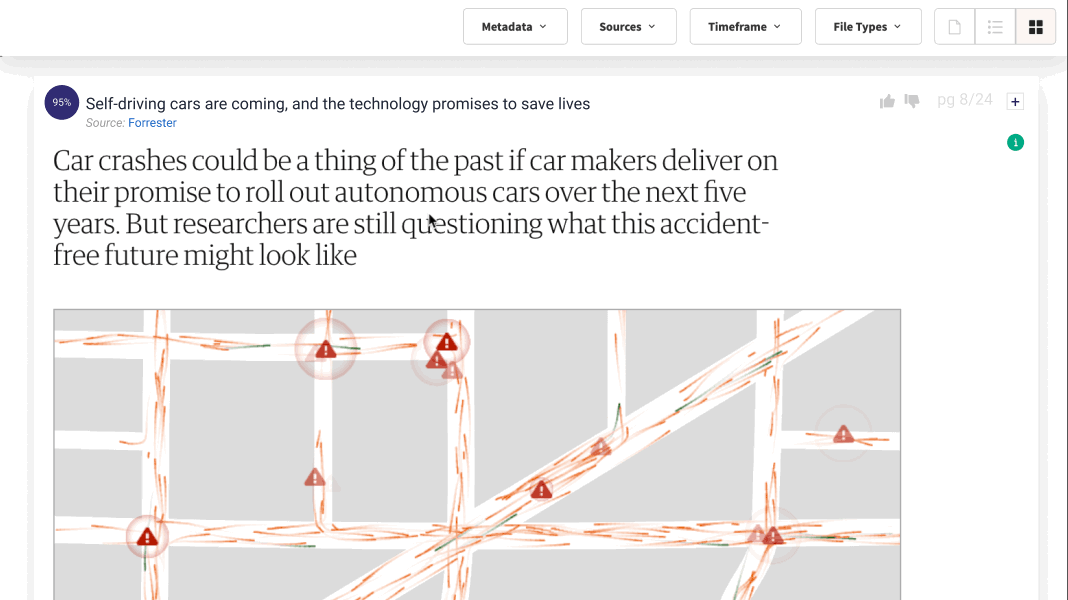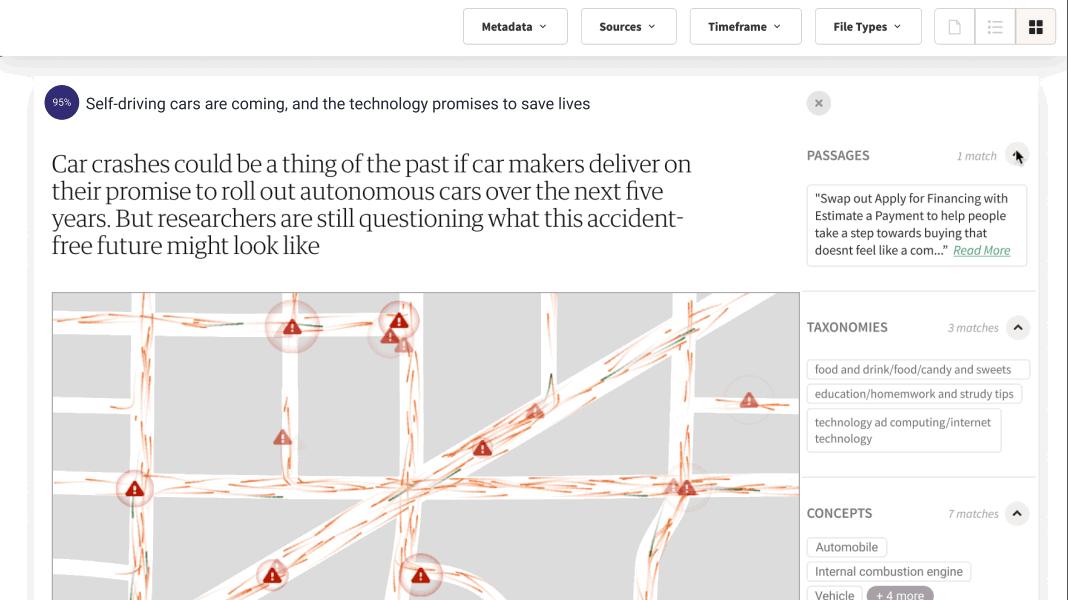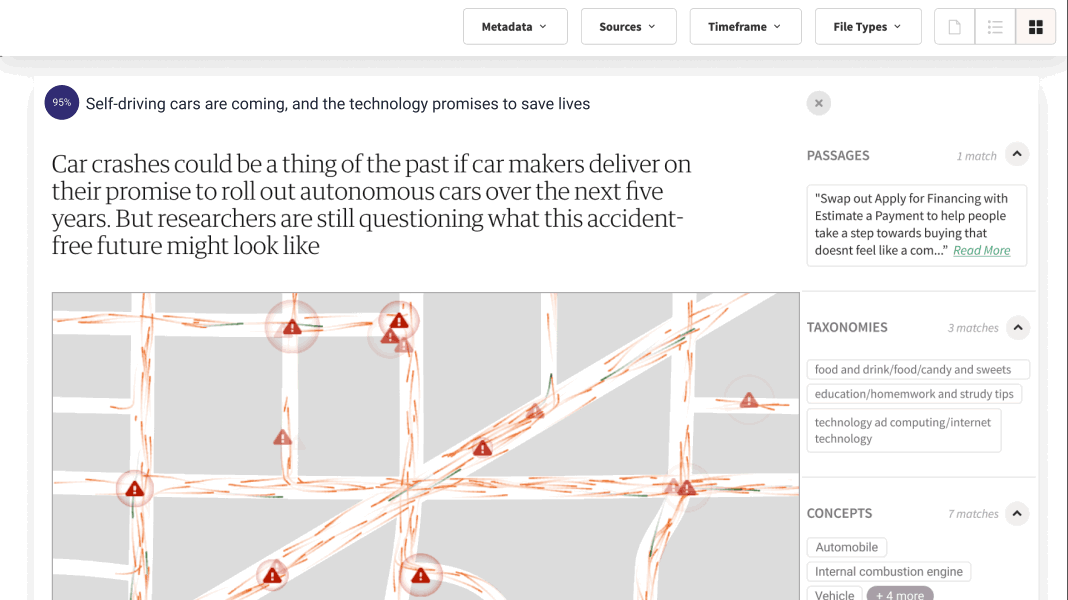
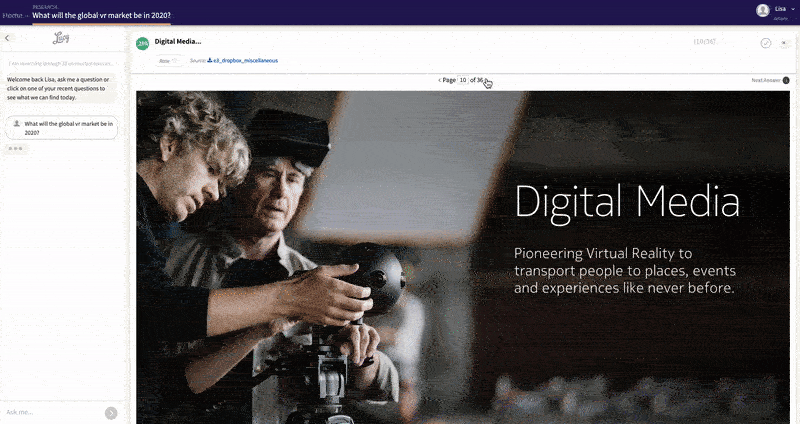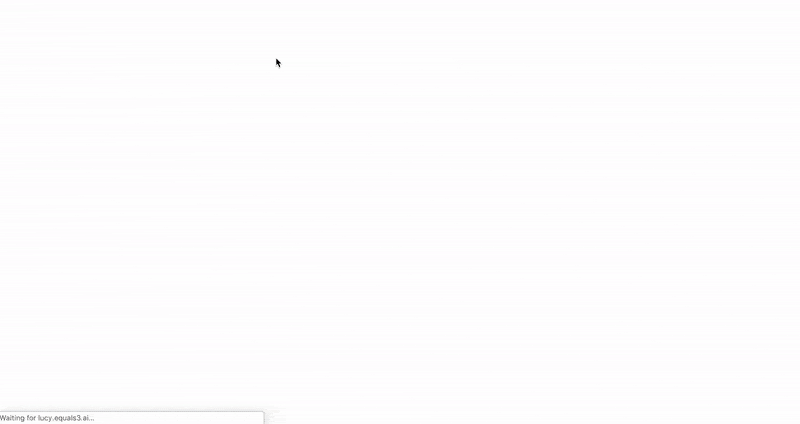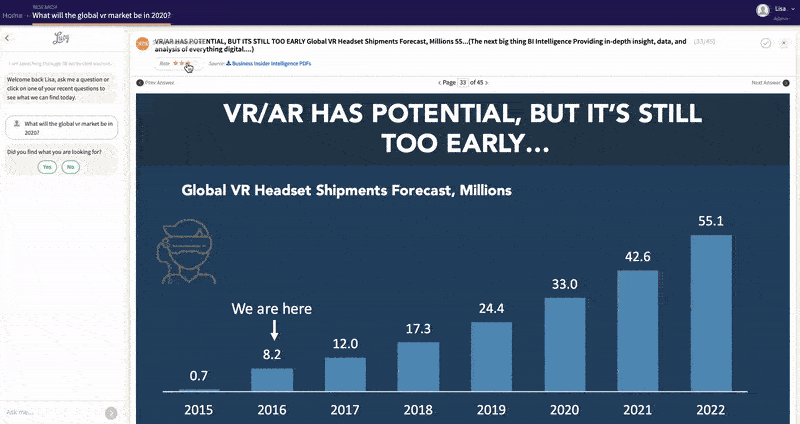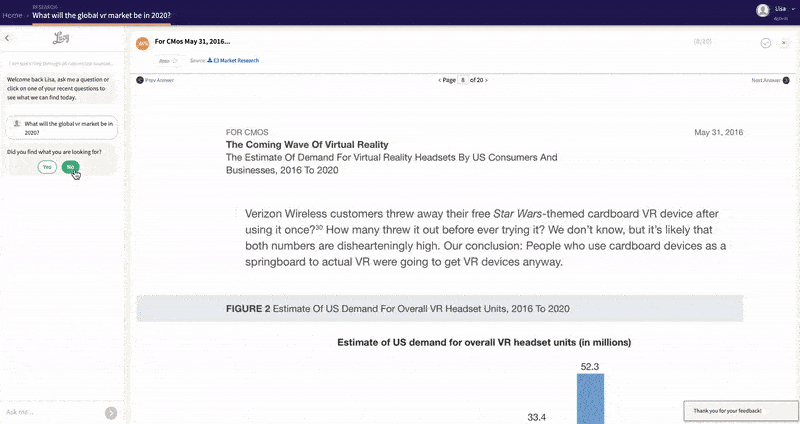
At Lucy, we understand the importance of data security for enterprise clients. That is why we have developed Lucy to prioritize data protection from the ground up, while seamlessly connecting to content at scale. With our ISO 27001 Certification dating back to 2020, Lucy upholds a steadfast dedication to the highest standards of data security. Hosted on Microsoft Azure, Lucy ensures the confidentiality, security, and compliance of your valuable data. Moreover, Lucy offers the flexibility of being hosted in your company's Microsoft Azure Private Cloud Tenant or your tenant in Microsoft Azure Government Cloud.
A Culture of Data Confidentiality
Recognizing that our greatest asset is the trust our clients place in us, we have made data security a cornerstone of our corporate ethos. We implement robust encryption, access controls, and compliance measures to safeguard your sensitive information against unauthorized access or disclosure both internally and externally. Combining the immense security capabilities of Microsoft Azure with Lucy’s culture of security and data privacy ensures your organization’s data stays safe.
Lucy’s Arsenal of Security Features
- End-to-End Encryption: Lucy’s encryption capabilities ensure that your data is encrypted both at rest and in transit, providing an impenetrable layer of protection against unauthorized interception.
- Single Sign on (SSO) and User Access Controls: We implement stringent access controls, multi-factor authentication (MFA), and role-based access to restrict access to authorized personnel only.
- Regulatory Compliance: Lucy teamed with Azure provides adherence to global compliance standards including ISO, GDPR, CCPA/CPRA, HIPAA, and SOC, we ensure that our data security practices align with regulatory requirements and industry best practices.
- Web Application Security: Lucy employs industry-standard web application firewalls which monitor traffic, prevent malicious intrusion, and protect our infrastructure from certain types of attacks. These capabilities not only help to keep our clients’ data secure, they also help to ensure the reliability, performance, and consistency that users expect from a modern web application.
- Lucy is an Answer Engine® Not a Document Manager: Lucy does not store documents only metadata. Your unmodified original document stays in your source system secured by your corporate policies and access.
- Retrieval Augmented Generation: Lucy pioneered the use of the Retrieval Augmented Generation approach. Lucy works without an LLM and optionally uses generative/LLM’s to help users leverage the answer’s Lucy as found. Through our expertise and generational advancements in application of this technology, your data stays safe because the LLM only receives what it needs to in order to provide a Lucy Synopsis(SM) or generative response.
- Private, Optional, Company Selectable GPT Services: Lucy understands that every organization is on its own path for the use of LLMs and GPTs. All of our GPT usage is private and enterprise-secure, you can provide your own model to be deployed, and you can even turn off GPT entirely while still getting all of the great benefits of the Answer Engine® for work.
- Lucy’s (IAM) Authorization: Lucy’s data access is defined by roles defined in the system. Only Authorized users have access to the information.
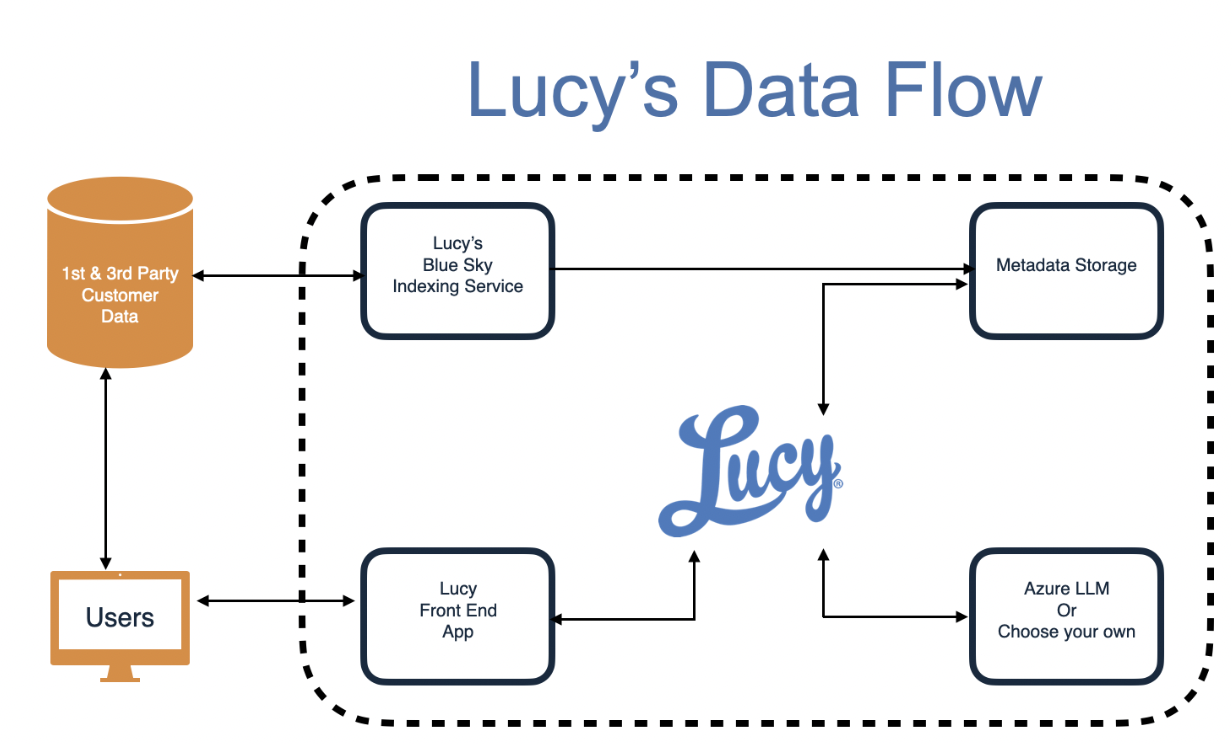
Secure, Read-Only Connection and Metadata Storage
When our clients authorize Lucy to connect to their data or system of record, we ensure that the connection is established securely and with their explicit consent to specific data resources. Upon creation of the read-only connection, a dedicated partition is created for metadata storage exclusively for the client, ensuring data isolation and confidentiality.
Automated Document Indexing and Metadata Generation
Once the sources are defined, our document Indexers spring into action, fetching authorized files and using our proprietary algorithms to generate rich metadata about them. This metadata enhances data organization, searchability, deeper insights and analysis for our clients. The original documents are never stored in Lucy or modified. They remain only in the source system of record.
Automated User and Source Provisioning
Depending on the client’s need, we support a wide range of strategies for provisioning users and the content they have access to. Lucy offers support for RFC 7642/7643/7644 or SCIM for user provisioning, connecting directly to our clients’ Microsoft Entra ID environment or similar identity management service where it makes sense. Source connectivity may be established at the highest level with Lucy automatically separating private access folders in the index so that only users with permission may search that content. We supply our clients with the tools they need to provision both company-shared and team-local sources in order to maximize the value of search to each user.
Role-based Access and User Empowerment
Users within our clients' organizations are granted access to data based on their access to source systems and documents, ensuring that each individual has access only to the information relevant to their responsibilities. Access control strengthens data security, fosters collaboration, and increases productivity within the organization.
Within Lucy, users are granted roles and attributes which manage secure access within the system. Roles and attributes are granted by either the admin, the auto-provisioning strategy, or a combination of both. User roles and attributes not only manage access but are also used for reporting and audit. The Lucy admin controls make it easy to see and manage one user, one role or attribute, and an overview of the landscape of all users and everything they have access to.
Lucy: Your Partner for Data Security
Through our standards, our processes, and our culture, Lucy is focused on world class data security so you can be assured your data is safe. We empower your employees with the information they need to learn more, achieve more, and save time. As your latest hire, from day one, Lucy is a champion of security at your company. In a world of amazing promises and demos coming from AI companies, Lucy has put in the work to ensure your data remains safe.