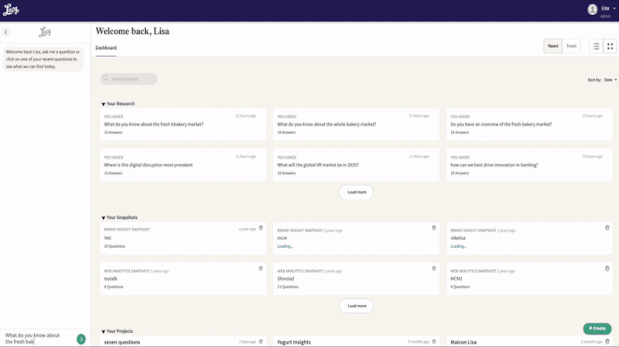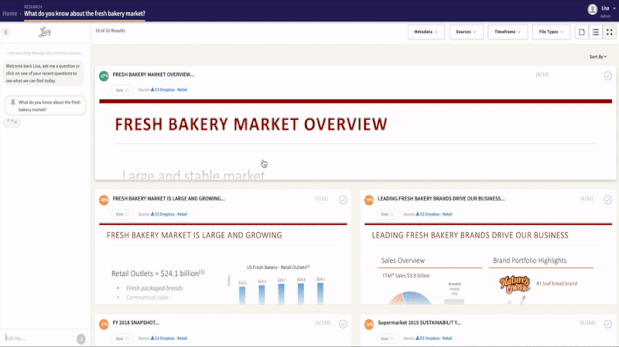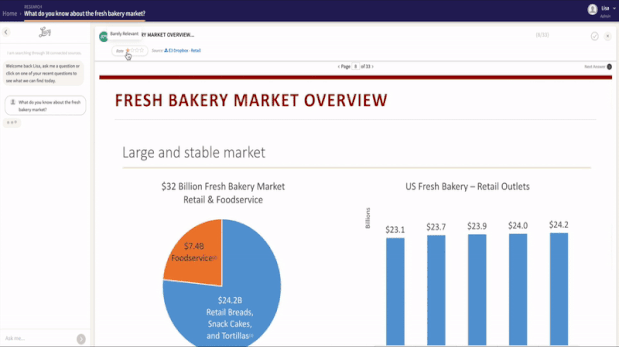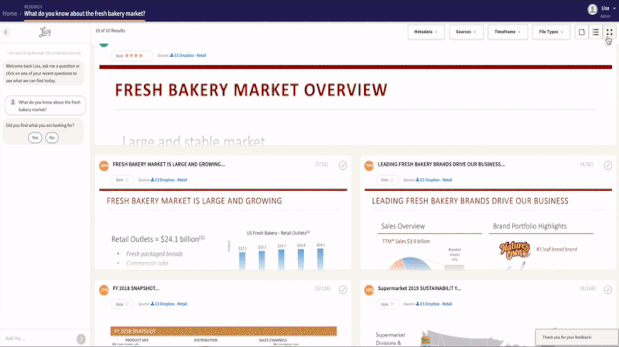
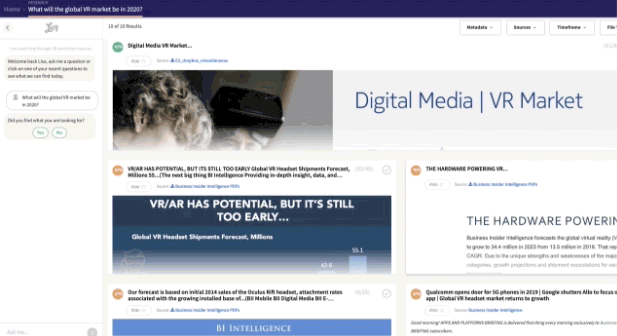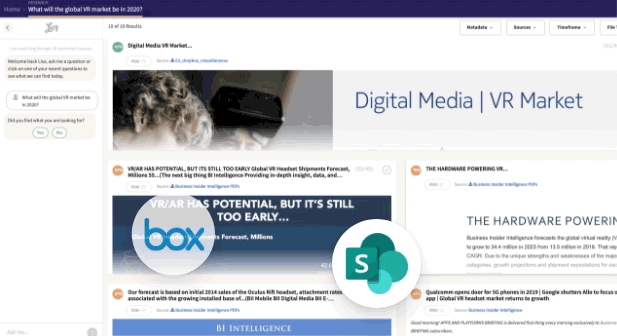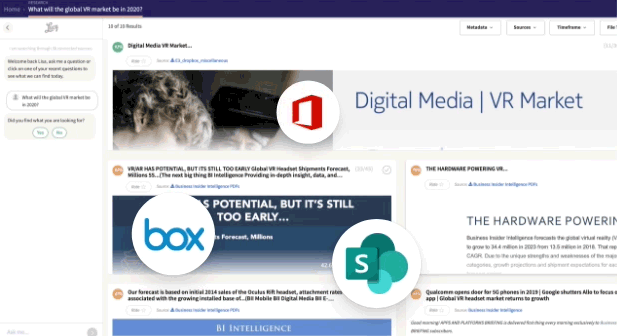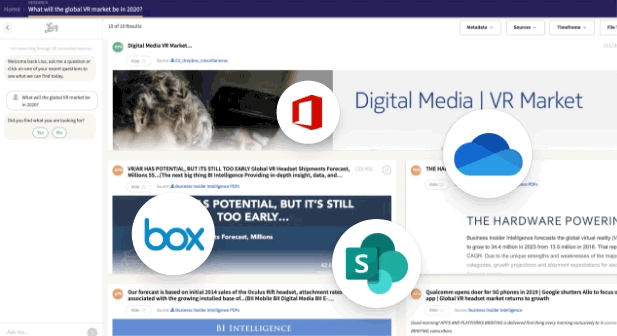
In an era where digital data proliferates at an unprecedented pace, finding the right information amidst the digital deluge is akin to navigating a complex maze. Traditional enterprise search engines, while powerful, often inundate us with a barrage of results, making it challenging to discern the relevant from the irrelevant. However, amidst this vast expanse of digital information, a revolutionary technology has emerged, promising to transform the way we interact with data in the enterprise. Enter the power of Retrieval-Augmented Generation (RAG) to redefine our relationship with information.
The internet, once seen as a source of knowledge for all, has now become a complex maze. Although traditional search engines are powerful, they often inundate users with a flood of results, making it difficult to find what they are searching for. The emergence of new technologies like ChatGPT from OpenAI has been impressive, along with other language models such as Bard. However, these models also come with certain drawbacks for business users, such as the risk of generating inaccurate information, a lack of proper citation, potential copyright infringements, and a scarcity of reliable information in the business domain. The challenge lies not only in finding information but in finding the right information. In order to make Generative AI effective in the business world, we must address these concerns, which is the focal point of RAG.
The digital challenge: A sea of information
At the corner of platforms like Microsoft Copilot and Lucy is the transformative approach of the Retrieval-Augmented Generation (RAG) model.
Understanding RAG
What precisely is RAG, and how does it work? In simple terms, RAG is a two-step process:
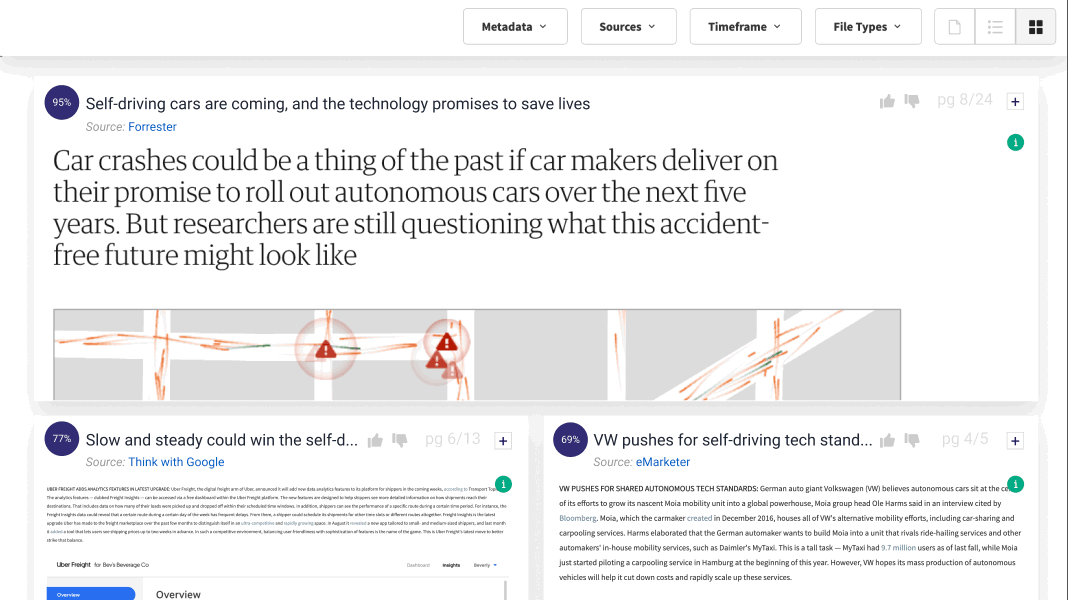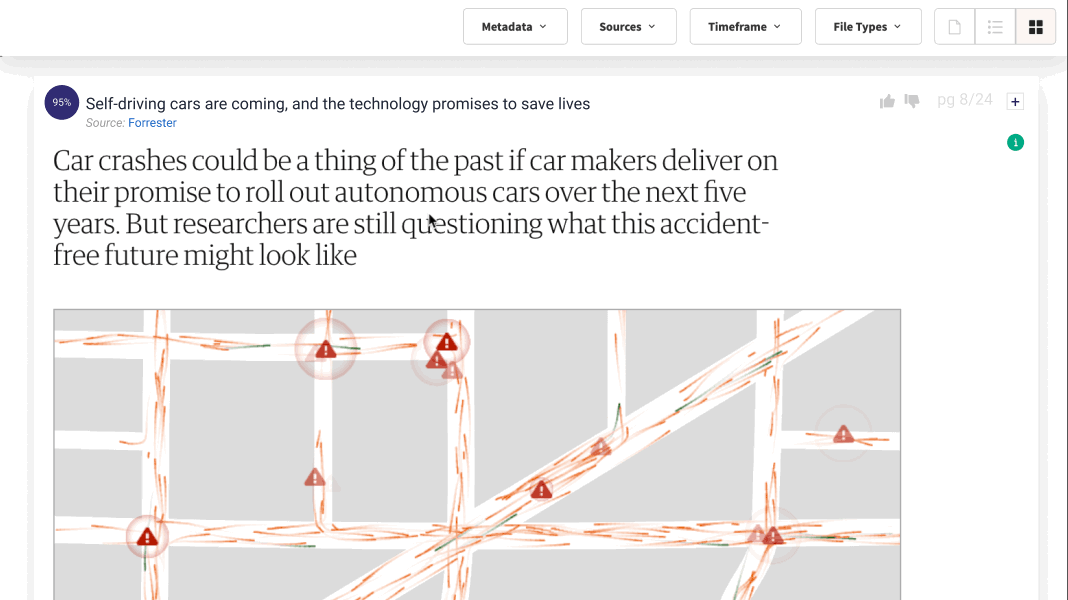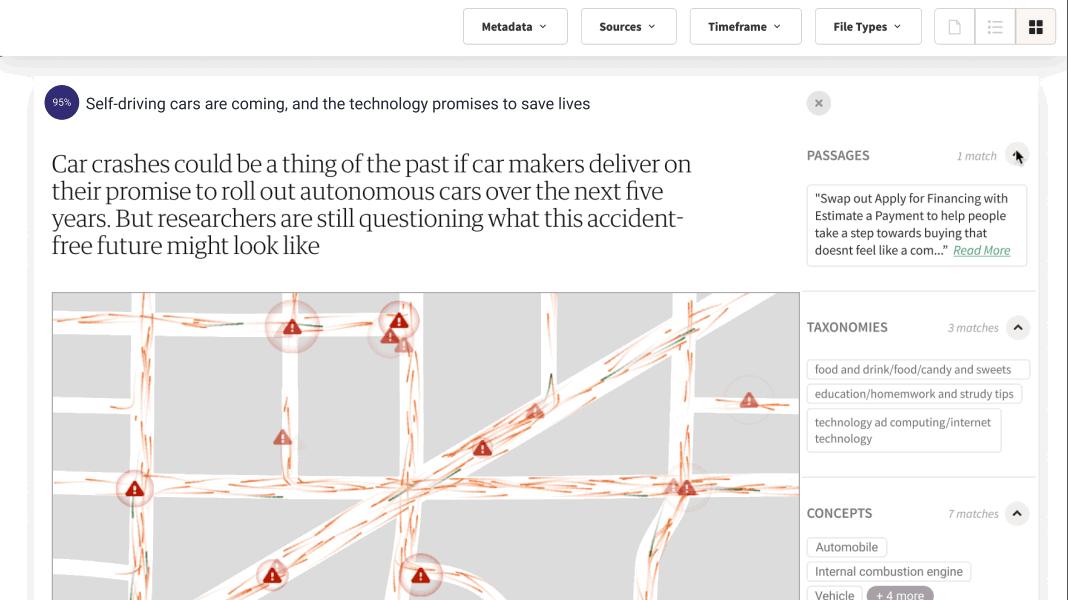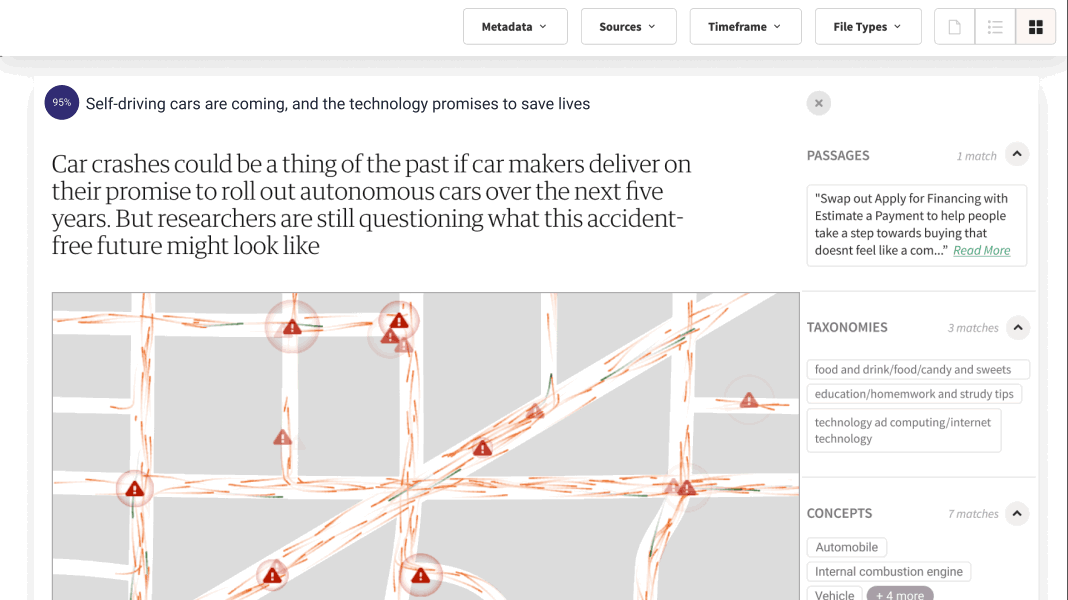
1. Retrieval: Prior to providing an answer, the system delves into an extensive database, meticulously retrieving pertinent documents or passages. This isn’t a rudimentary matching of keywords; it’s a cutting-edge process that comprehends the intricate context and nuances of the query. RAG systems rely on the data owned or licensed by companies, and ensure that Enterprise Levels of access control are impeccably managed and preserved.